Attack of the Clones: How Audits Protect Social Media Trademarks

During my first week as social media manager at Texas State University (@TXST) I opened my laptop to take a look at my listening dashboard and almost had a heart attack when I saw a post from an account called @TXSTstudents.

My first thought on seeing the name of the account and profile photo was that this was an official university account that had gone off the rails or possibly hacked. But after thirty seconds of investigation (and mild panic) it was clear that this was a student-run account.
The bio read: “Texas State page made by the students. Put #BobcatFamily in your bio to show your pride (Must attend TXST). Designed to increase school spirit #TXST (Fan Page).”
But here’s the clincher—it had 62,800 followers! The school’s official account only had around 60,000 at the time. Obviously, the account had tons of fake followers, but what was happening here?
Diving deeper, I noticed several accounts with similar names, (@TXSTcampus, @TXSTuniversity, @TXSTschool) posts, bios, and follower counts.
These accounts were purposely misleading, using university trademarks, duplicating posts from the university Twitter account, and photos from the university website in an effort to gain followers. These accounts then promoted parties and events in the local area.
In addition, there were several smaller accounts behaving in a similar manner that were following this lead. It was clear something had to be done. But how?
Universities are easy targets for impersonation accounts and trademark misuse. They’re often created by students and, while some have good intentions, many are hoping to quickly gain a large following and cause general mischief. They also tend to grow rapidly because schools are often slow to notice and take the appropriate measures to protect their trademarks and shut these accounts down. But make no mistake, these accounts can quickly change the perception of your institution—they hurt your brand strategy, your brand, and even worse, can be used for bullying and harassment.
These simple steps can identify and stop these accounts so you can protect your social media trademarks before the accounts damage your school’s reputation.
Make an Audit and Categorize
You need to get an idea of how big the problem is and become familiar with what you're dealing with. Perform an audit to find all non-university affiliated accounts that are using your trademarks or your school’s name. Create a list of suspicious accounts in whatever social listening platform you’re using in order to follow them and monitor their activity.
From there you need to categorize them as to what sort of account they are. Twitter allows for what it refers to as “fan, newsfeed, parody, or commentary” accounts. We’ve all seen these. They often have names like @NotTheBobcats or @BobcatFans. While these accounts might be critical of your university or minor nuisances they’re acting within the rules of Twitter policy and it’s often best to leave these accounts alone. However, when an account is actively violating your trademarks in order to mislead the public, this is an impersonation account and action needs to be taken.
At Texas State, the problem was rampant. After an audit, nearly thirty accounts were found to be actively misleading, many with more than 25,000 followers.
Catalog Examples of Brand Impersonation
As you monitor these accounts, collect examples of how they are violating trademarks. Are they using your logo as their avatar? Are they using your photos in their posts? Are they actively copying your content? This was the issue at Texas State. The following posts clearly show the original content from @TXST on the left and the stolen content from the impersonation account on the right.
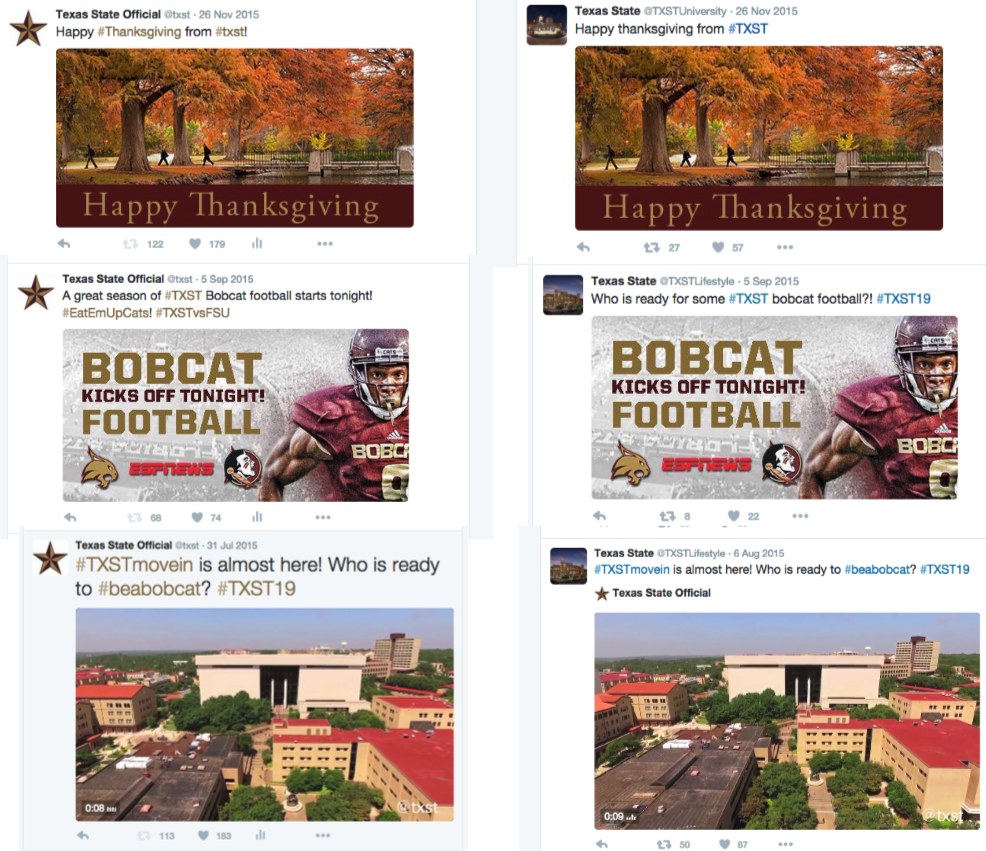
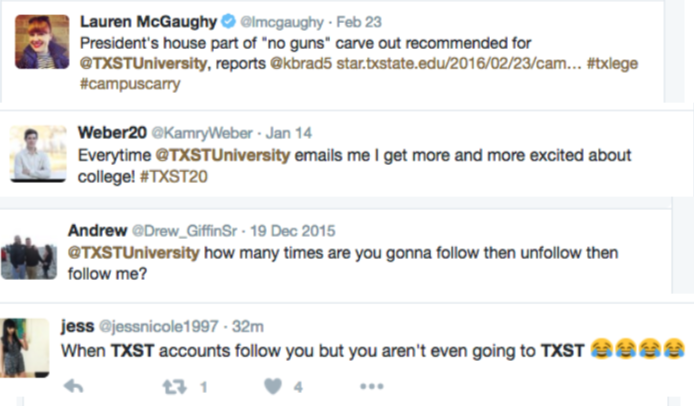
In addition to monitoring the offending accounts, use social listening to determine the confusion these accounts are causing among your community and catalog the examples. The examples from prospective students refer to the wrong Twitter account in their posts and there’s even a post from a local reporter using the handle of an impersonation account.
File Trademark Complaints with Twitter
Once you catalog some examples you can clearly determine the accounts that are most clearly violating Twitter’s terms of service. These are the accounts that use your university’s trademarked logos or name without any indication that they're parody or fan accounts.
Speak with your university’s trademark officer or attorney and request:
- Trademark Class Number
- Trademark Registration Number
- Letter of Complaint
For the letter of complaint, I had the university counsel write up something that I could use multiple times and insert the proper names and issues as necessary.

When accounts are in clear violation of trademark issues, Twitter reacts fairly quickly. They’ll send a notice to the offending account informing them that they have 48 hours to comply by removing the trademarked images or name from their account. If they don’t, Twitter will remove their account, however, it’s on you as the complainant to inform Twitter if the account doesn’t comply within the allotted time.
Set a timer for 48 hours and have an email to Twitter ready to go in each instance. The moment the 48 hours is up, if the account didn't comply, send Twitter your email to let them know that the account is still in violation and needs to be removed. In my experience, very few accounts complied with Twitter’s request and their accounts were deleted.
File Cease and Desist Letters
For Texas State, several of the impersonation accounts included the term “Fan Account” in their bio. In the eyes of Twitter, this is enough to allow the account to remain open, despite the trademark use and copied content. These cases required us to use stronger techniques. After engaging in the social listening discussion surrounding these accounts from students, we determined the person behind several of the larger accounts. It was a student and self-proclaimed “social media influencer” who used the accounts as a platform for advertising local events and parties, sell vitamin supplements, and even a brand of pre-mixed cocktails! Once we found the person behind the accounts, we worked with university counsel to send a cease and desist letter informing the account owner to stop using university trademarks or face a lawsuit. Within 48 hours of receiving the letter, the account owner changed the account names and removed all university-owned images. If you’re unable to determine the person behind the account, you can also send the cease and desist letter via direct message to the offending account.
Last Resort
If the cease and desist letters don’t work, then it’s time to lawyer up and take them to court. By this point, you’ve already talked to your university attorneys and compiled evidence for your case. It’s never come to this in my experience, but I know at Texas State our university counsel was ready to go and even eager to present a case like this.
At Texas State, the cease and desist letters ended our clones. They changed their names and stopped using our content. And while they were still a thorn in our side, they were severely weakened after this. Eventually, the student running the accounts graduated and moved on. (He’s now using the accounts to promote his weightlifting career and gain clout as an “influencer.”)
Also, once word got around that we were going after social accounts that misused our trademarks, the number of accounts doing this lowered significantly and we now have a seamless process for reporting and dealing with these instances when they do occur.
Don't want to miss a single post from Campus Sonar? Subscribe to our monthly Brain Waves newsletter to get the latest and greatest about social listening in higher education delivered right to your inbox.
The post Attack of the Clones: How an Audit Can Protect Your University's Social Media Trademarks originally appeared on the Campus Sonar Brain Waves blog.
